The Cisco 350-201 Performing CyberOps Using Cisco Security Technologies (CBRCOR) exam is a critical step for cybersecurity professionals aiming to validate their skills in security monitoring, incident response, and automation. To help you succeed in the 2025 Cisco certification, our online practice exam features the latest questions and answers sourced from Leads4Pass, ensuring you stay ahead of the curve.
By sharing these real-time updated resources on Brain2dumps, we help candidates prepare efficiently and boost confidence for exam day. The following 350-201 CBRCOR exam questions and answers will keep you one step ahead with cutting-edge insights!
Share 350-201 CBRCOR exam questions and answers online
| Number of exam questions (Free) | Total Questions |
| 15 Q&A | 139 Q&A |
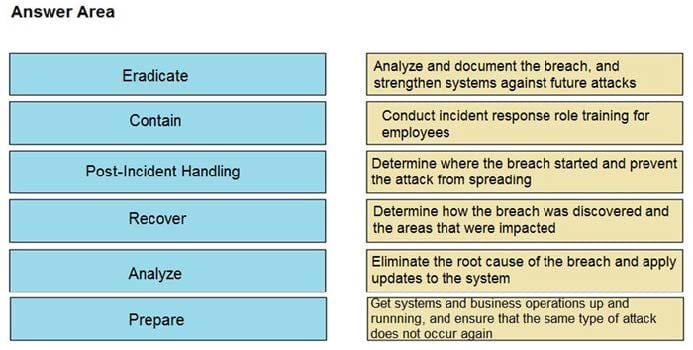
Question 1:
DRAG DROP
Drag and drop the NIST incident response process steps from the left onto the actions that occur in the steps on the right.
Select and Place:
Correct Answer:
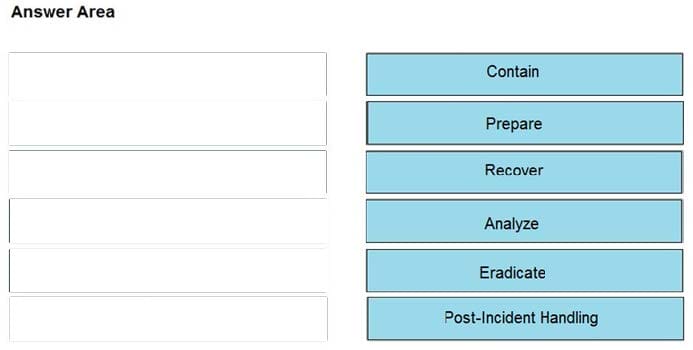
Reference: https://www.securitymetrics.com/blog/6-phases-incident-response-plan
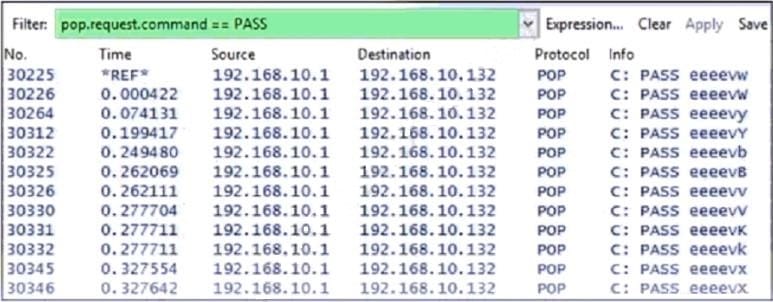
Question 2:
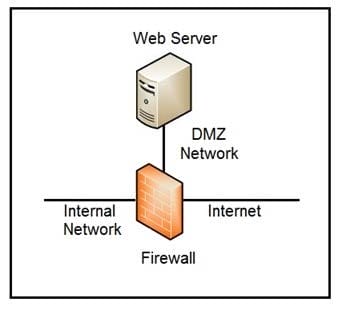
Refer to the exhibit. Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
A. Create an ACL on the firewall to allow only TLS 1.3
B. Implement a proxy server in the DMZ network
C. Create an ACL on the firewall to allow only external connections
D. Move the webserver to the internal network
Correct Answer: BD
Question 3:
DRAG DROP
Drag and drop the mitigation steps from the left onto the vulnerabilities they mitigate on the right.
Select and Place:
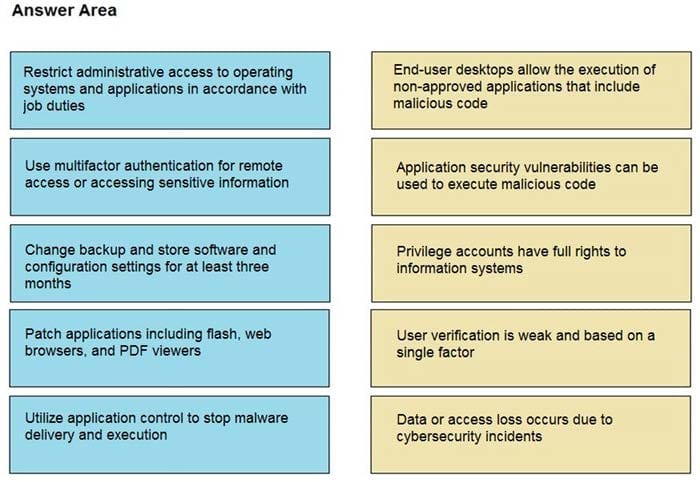
Correct Answer:
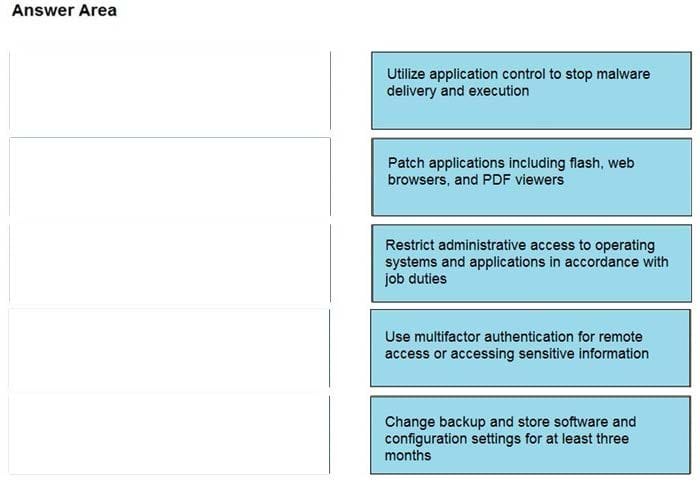
Question 4:
A SOC analyst detected a ransomware outbreak in the organization coming from a malicious email attachment. Affected parties are notified, and the incident response team is assigned to the case. According to the NIST incident response handbook, what is the next step in handling the incident?
A. Create a follow-up report based on the incident documentation.
B. Perform a vulnerability assessment to find existing vulnerabilities.
C. Eradicate malicious software from the infected machines.
D. Collect evidence and maintain a chain-of-custody during further analysis.
Correct Answer: D
Question 5:
An analyst is alerted for a malicious file hash. After analysis, the analyst determined that an internal workstation is communicating over port 80 with an external server and that the file hash is associated with Duqu malware. Which tactics, techniques, and procedures align with this analysis?
A. Command and Control, Application Layer Protocol, Duqu
B. Discovery, Remote Services: SMB/Windows Admin Shares, Duqu
C. Lateral Movement, Remote Services: SMB/Windows Admin Shares, Duqu
D. Discovery, System Network Configuration Discovery, Duqu
Correct Answer: A
Question 6:
What do 2xx HTTP response codes indicate for REST APIs?
A. additional action must be taken by the client to complete the request
B. the server takes responsibility for error status codes
C. communication of transfer protocol-level information
D. successful acceptance of the client\’s request
Correct Answer: D
Question 7:
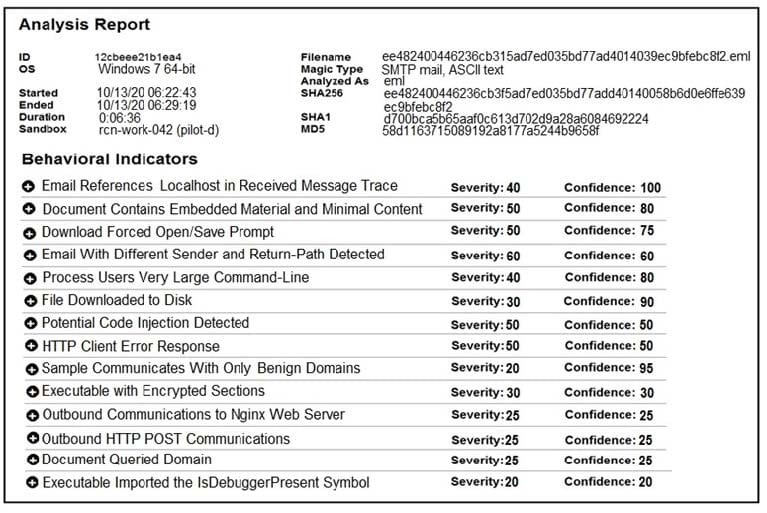
Refer to the exhibit. Cisco Advanced Malware Protection installed on an end-user desktop automatically submitted a low prevalence file to the Threat Grid analysis engine. What should be concluded from this report?
A. Threat scores are high, malicious ransomware has been detected, and files have been modified
B. Threat scores are low, malicious ransomware has been detected, and files have been modified
C. Threat scores are high, malicious activity is detected, but files have not been modified
D. Threat scores are low and no malicious file activity is detected
Correct Answer: B
Question 8:
A payroll administrator noticed unexpected changes within a piece of software and reported the incident to the incident response team. Which actions should be taken at this step in the incident response workflow?
A. Classify the criticality of the information, research the attacker\’s motives, and identify missing patches
B. Determine the damage to the business, extract reports, and save evidence according to a chain of custody
C. Classify the attack vector, understand the scope of the event, and identify the vulnerabilities being exploited
D. Determine the attack surface, evaluate the risks involved, and communicate the incident according to the escalation plan
Correct Answer: B
Question 9:
An engineer returned to work and realized that payments that were received over the weekend were sent to the wrong recipient. The engineer discovered that the SaaS tool that processes these payments was down over the weekend. Which step should the engineer take first?
A. Utilize the SaaS tool team to gather more information on the potential breach
B. Contact the incident response team to inform them of a potential breach
C. Organize a meeting to discuss the services that may be affected
D. Request that the purchasing department creates and sends the payments manually
Correct Answer: A
Question 10:
Employees receive an email from an executive within the organization that summarizes a recent security breach and requests that employees verify their credentials through a provided link. Several employees report the email as suspicious, and a security analyst is investigating the reports. Which two steps should the analyst take to begin this investigation? (Choose two.)
A. Evaluate the intrusion detection system alerts to determine the threat source and attack surface.
B. Communicate with employees to determine who opened the link and isolate the affected assets.
C. Examine the firewall and HIPS configuration to identify the exploited vulnerabilities and apply recommended mitigation.
D. Review the mail server and proxy logs to identify the impact of a potential breach.
E. Check the email header to identify the sender and analyze the link in an isolated environment.
Correct Answer: CE
Question 11:
DRAG DROP
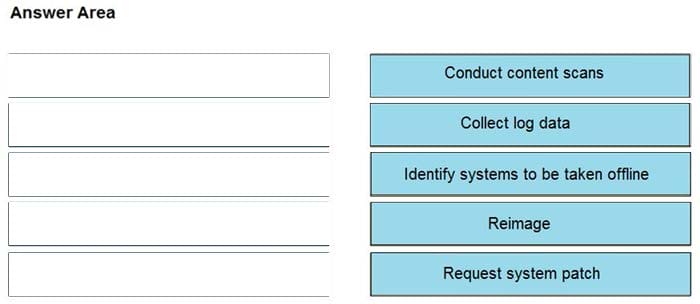
An engineer notices that unauthorized software was installed on the network and discovers that it was installed by a dormant user account. The engineer suspects an escalation of privilege attack and responds to the incident. Drag and drop the activities from the left into the order for the response on the right.
Select and Place:
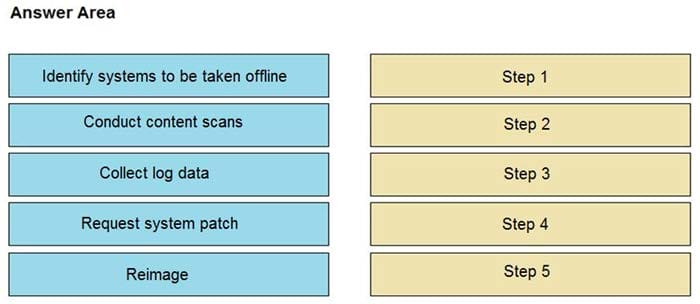
Correct Answer:
Question 12:
Refer to the exhibit. Which command was executed in PowerShell to generate this log?
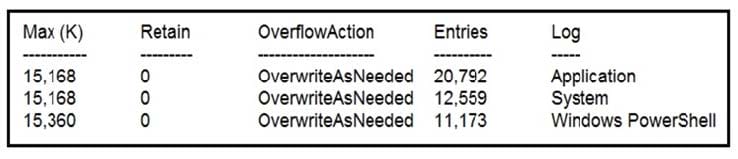
A. Get-EventLog -LogName*
B. Get-EventLog -List
C. Get-WinEvent -ListLog* -ComputerName localhost
D. Get-WinEvent -ListLog*
Correct Answer: A
Reference: https://lists.xymon.com/archive/2019-March/046125.html
Question 13:
An organization had several cyberattacks over the last 6 months and has tasked an engineer with looking for patterns or trends that will help the organization anticipate future attacks and mitigate them. Which data analytic technique should the engineer use to accomplish this task?
A. diagnostic
B. qualitative
C. predictive
D. statistical
Correct Answer: C
Question 14:
Refer to the exhibit. Based on the detected vulnerabilities, what is the next recommended mitigation step?
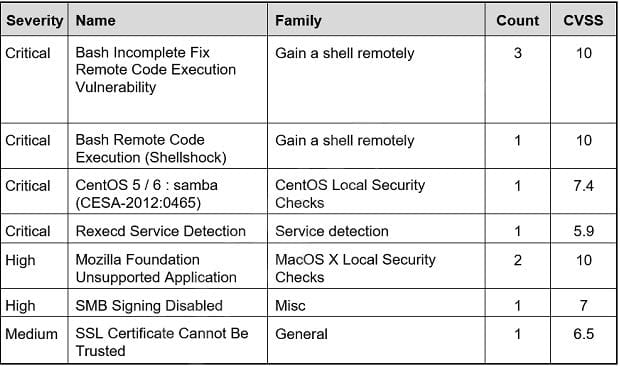
A. Evaluate service disruption and associated risk before prioritizing patches.
B. Perform root cause analysis for all detected vulnerabilities.
C. Remediate all vulnerabilities with descending CVSS score order.
D. Temporarily shut down unnecessary services until patch deployment ends.
Correct Answer: B
Question 15:
A security expert is investigating a breach that resulted in a $32 million loss from customer accounts. Hackers were able to steal API keys and two-factor codes due to a vulnerability that was introduced in a new code a few weeks before the attack.
Which step was missed that would have prevented this breach?
A. use of the Nmap tool to identify the vulnerability when the new code was deployed
B. implementation of a firewall and intrusion detection system
C. implementation of an endpoint protection system
D. use of SecDevOps to detect the vulnerability during development
Correct Answer: D
Reference: https://securityintelligence.com/how-to-prioritize-security-vulnerabilities-in-secdevops/
…
The value of the latest exam questions is undeniable. The current 350-201 CBRCOR practice exam includes 139 questions with real-world scenarios.
| Single & multiple choice | 126 Q&As |
| Drag drop | 13 Q&As |
| Free Download | 15 Q&As (PDF) |
FAQs
Are the practice questions updated regularly to reflect the 2025 exam?
Yes, our community on Brain2dumps continuously updates the question bank with contributions from Leads4Pass and other reliable sources to align with the latest exam objectives.
What are the technical requirements for using the practice exam platform?
A stable internet connection and a modern browser (Chrome, Firefox, or Safari) are sufficient. The platform is compatible with both mobile and desktop devices.
How do the practice questions help with real-world scenarios?
The Leads4Pass practice questions include real-world scenarios that mirror the exam’s focus on security monitoring, incident response, and automation, preparing you for practical challenges.
I want to tell you
The Cisco 350-201 CBRCOR certification is a key step in advancing your cybersecurity career, and practicing with the latest questions is crucial for success. Through scenario-based questions shared on Brain2dumps, sourced from trusted providers like Leads4Pass, you gain access to cutting-edge resources aligned with the 2025 exam objectives. Start preparing today, engage with fellow candidates, and take the first step toward earning your CBRCOR certification!