
leads4pass has updated Fortinet NSE 6-Secure Wireless LAN 6.4 – NSE6_FWF-6.4 dumps, NSE6_FWF-6.4 dumps contains two modes PDF and VCE, choose anyone to help you pass the exam easily!
All exam questions are actually valid and verified by Fortinet experts. NSE6_FWF-6.4 belongs to the Cybersecurity Technical Certification exam category, and passing the exam will increase your professional worth. Now, get the latest NSE6_FWF-6.4 dumps from leads4pass: https://www.leads4pass.com/nse6_fwf-6-4.html (Total Questions: 30 Q&A).
The most important thing is for leads4pass to share part of the NSE6_FWF-6.4 exam PDF for free:
Google Drive: https://drive.google.com/file/d/1FiZ9RbCs7LAFc7ZdYgpuqgowuOnglKo1/view?usp=sharing
Fortinet NSE6_FWF-6.4 Exam Questions Online Test
Online test to verify the strength, and finally, verify the answer at the end of the article
QUESTION 1
How are wireless clients assigned to a dynamic VLAN configured for hash mode?
A. Using the current number of wireless clients connected to the SSID and the number of IPs available in the least busy VLAN
B. Using the current number of wireless clients connected to the SSID and the number of clients allocated to each of the VLANs
C. Using the current number of wireless clients connected to the SSID and the number of VLANs available in the pool
D. Using the current number of wireless clients connected to the SSID and the group the FortiAP is a member of VLAN from the VLAN pool based on a hash of the current number of SSID clients and the number of entries in the VLAN pool.
QUESTION 2
Which two configurations are compatible for Wireless Single Sign-On (WSSO)? (Choose two.)
A. A VAP configured for captive portal authentication
B. A VAP configured for WPA2 or 3 Enterprise
C. A VAP configured to authenticate locally on FortiGate
D. A VAP configured to authenticate using a radius server
In the SSID choose WPA2-Enterprise authentication.
WSSO is RADIUS-based authentication that passes the user\\’s user group memberships to the FortiGate.
Reference: https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/b92a67f9-73a6-11ea9384-00505692583a/FortiWiFi_and_FortiAP-6.4.2-Configuration_Guide.pdf
QUESTION 3
Where in the controller interface can you find a wireless client\\’s upstream and downstream link rates?
A. On the AP CLI, using the cw_diag ksta command
B. On the controller CLI, using the diag wireless-controller wlac -d sta command
C. On the AP CLI, using the cw_diag -d sta command
D. On the controller CLI, using the WiFi Client monitor
QUESTION 4
Refer to the exhibits.
Exhibit A Exhibit B
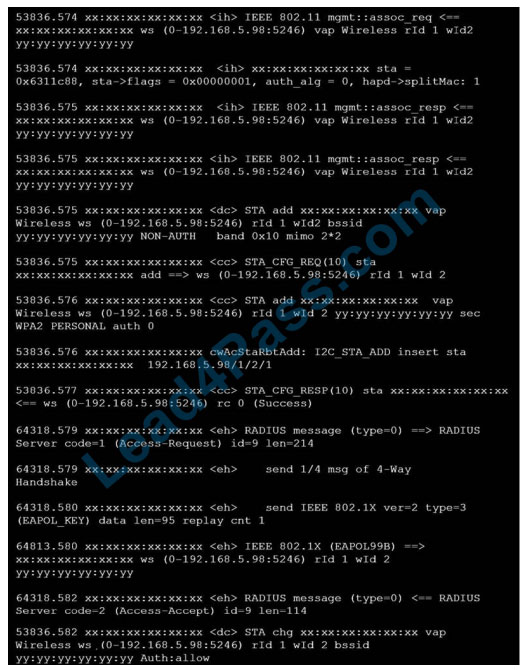
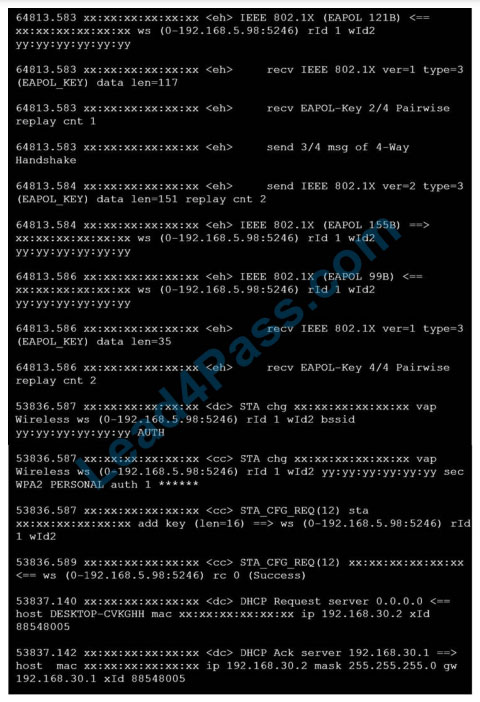
The exhibits show the diagnose debug log of a station connection taken on the controller CLI. Which security mode is used by the wireless connection?
A. WPA2 Enterprise
B. WPA3 Enterprise
C. WPA2 Personal and radius MAC filtering
D. Open, with radius MAC filtering
Best security option is WPA2-AES.
Reference: https://www.esecurityplanet.com/trends/the-best-security-for-wireless-networks/
QUESTION 5
As a network administrator, you are responsible for managing an enterprise secure wireless LAN. The controller is based in the United States, and you have been asked to deploy a number of managed APs in a remote office in Germany.
What is the correct way to ensure that the RF channels and transmission power limits are appropriately configured for the remote APs?
A. Configure the APs individually by overriding the settings in Managed FortiAPs
B. Configure the controller for the correct country code for Germany
C. Clone a suitable FortiAP profile and change the county code settings on the profile
D. Create a new FortiAP profile and change the county code settings on the profile
Reference: https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/69a8fa9c-1eaa-11e9b6f6-f8bc1258b856/fortigate-fortiwifi-and-fortiap-configuration-guide-54.pdf
QUESTION 6
Which of the following is a requirement to generate analytic reports using on-site FortiPresence deployment?
A. SQL services must be running
B. Two wireless APs must be sending data
C. DTLS encryption on wireless traffic must be turned off
D. Wireless network security must be set to open
FortiPresence VM is deployed locally on your site and consists of two virtual machines. All the analytics data collected and computed resides locally on the VMs.
QUESTION 7
Which two roles does FortiPresence analytics assist in generating presence reports? (Choose two.)
A. Gathering details about on site visitors
B. Predicting the number of guest users visiting on-site
C. Comparing current data with historical records
D. Reporting potential threats by guests on site
QUESTION 8
Refer to the exhibits.
Exhibit A
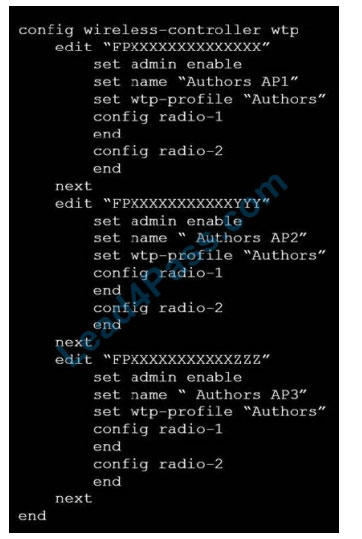
Exhibit B
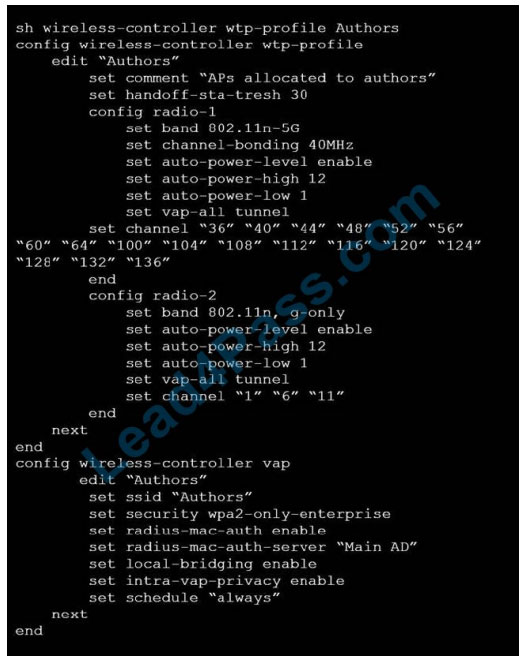
A wireless network has been created to support a group of users in a specific area of a building. The wireless network is configured but users are unable to connect to it. The exhibits show the relevant controller configuration for the APs and the wireless network.
Which two configuration changes will resolve the issue? (Choose two.)
A. For both interfaces in the wtp-profile, configure set vaps to be “Authors”
B. Disable intra-vap-privacy for the Authors vap-wireless network
C. For both interfaces in the wtp-profile, configure vap-all to be manual
D. Increase the transmission power of the AP radio interfaces
QUESTION 9
Which two statements about distributed automatic radio resource provisioning (DARRP) are correct? (Choose two.)
A. DARRP performs continuous spectrum analysis to detect sources of interference. It uses this information to allow the AP to select the optimum channel.
B. DARRP performs measurements of the number of BSSIDs and their signal strength (RSSI). The controller then uses this information to select the optimum channel for the AP.
C. DARRP measurements can be scheduled to occur at specific times.
D. DARRP requires that wireless intrusion detection (WIDS) be enabled to detect neighboring devices.
DARRP (Distributed Automatic Radio Resource Provisioning) technology ensures the wireless infrastructure is always optimized to deliver maximum performance. Fortinet APs enabled with this advanced feature continuously monitor the RF environment for interference, noise and signals from neighboring APs, enabling the FortiGate WLAN Controller to determine the optimal RF power levels for each AP on the network. When a new AP is provisioned, DARRP also ensures that it chooses the optimal channel, without administrator intervention.
Reference: http://www.corex.at/Produktinfos/FortiOS_Wireless.pdf
QUESTION 10
When enabling security fabric on the FortiGate interface to manage FortiAPs, which two types of communication channels are established between FortiGate and FortiAPs? (Choose two.)
A. Control channels
B. Security channels
C. FortLink channels
D. Data channels
The control channel for managing traffic, which is always encrypted by DTLS. l The data channel for carrying client data packets.
QUESTION 11
Which two statements about background rogue scanning are correct? (Choose two.)
A. A dedicated radio configured for background scanning can support the connection of wireless clients
B. When detecting rogue APs, a dedicated radio configured for background scanning can suppress the rogue AP
C. Background rogue scanning requires DARRP to be enabled on the AP instance
D. A dedicated radio configured for background scanning can detect rogue devices on all other channels in its configured frequency band.
To enable rogue AP scanning
Reference: https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/723e20ad-509811e9-94bf-00505692583a/FortiWiFi_and_FortiAP-6.2.0-Configuration_Guide.pdf
QUESTION 12
Which administrative access method must be enabled on a FortiGate interface to allow APs to connect and function?
A. Security Fabric
B. SSH
C. HTTPS
D. FortiTelemetry
QUESTION 13
Refer to the exhibit.
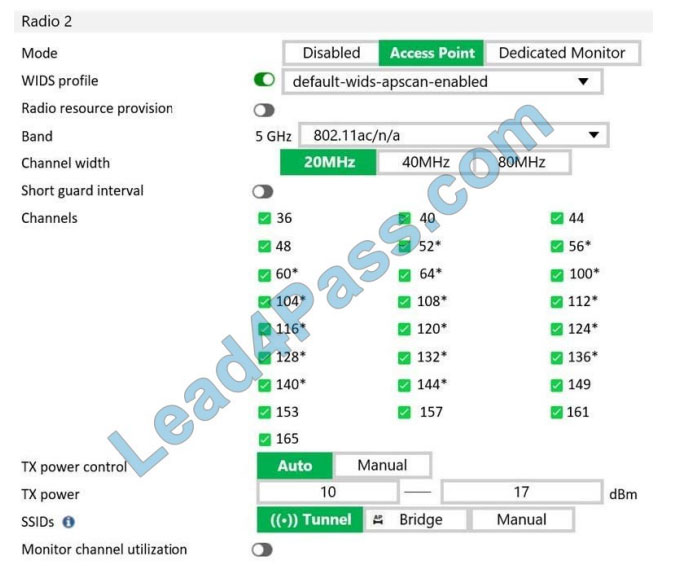
What does the asterisk (*) symbol beside the channel mean?
A. Indicates channels that can be used only when Radio Resource Provisioning is enabled
B. Indicates channels that cannot be used because of regulatory channel restrictions
C. Indicates channels that will be scanned by the Wireless Intrusion Detection System (WIDS)
D. Indicates channels that are subject to dynamic frequency selection (DFS) regulations
Verify the answer:
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 |
| C | BD | B | A | C | B | AB | BC | AD | AD | AB | A | A |
More Fortinet NSE6_FWF-6.4 exam questions -> Use VCE and PDF to learn leads4pass NSE6_FWF-6.4 dump to ensure that the first exam is successfully passed: https://www.leads4pass.com/nse6_fwf-6-4.html (Total Questions: 30 Q&A )
Thanks for reading! Cybersecurity Technical Certification is Fortinet’s basic certification. Obtained Fortinet NSE6_FWF-6.4 certification and entered the Fortinet family.


Comments are closed.