Leads4Pass CyberOps Associate 200-201 Dumps has been updated! It is the latest exam preparation material for 200-201 CBROPS “Understanding Cisco Cybersecurity Operations Fundamentals”!
The 2024 Leads4Pass CyberOps Associate 200-201 Dumps contains 322 latest exam questions and answers. The difficult questions provide answer analysis and graphic introduction to help you learn easily and improve your academic performance.
Download Leads4Pass CyberOps Associate 200-201 Dumps: https://www.leads4pass.com/200-201.html (choose PDF or VCE to help you practice exams), 100% guaranteed that you will successfully pass the exam.
Exam Practice:
Leads4Pass CyberOps Associate 200-201 dumps exam questions shared online
| From | Number of exam questions (Free) | Types | Test focus | Related certifications |
| Leads4Pass | 15/322 | Single-selection and multiple-selection | 1. Security concepts 2. Security monitoring 3. Host-based analysis 4. Network intrusion analysis Security 5. policies and procedures | CCNA |
Question 1:
A security expert is working on a copy of the evidence, an ISO file that is saved in CDFS format. Which type of evidence is this file?
A. CD data copy prepared in Windows
B. CD data copy prepared in a Mac-based system
C. CD data copy prepared in Linux system
D. CD data copy prepared in Android-based system
Correct Answer: A
Question 2:
What are the two characteristics of the full packet captures? (Choose two.)
A. Identifying network loops and collision domains.
B. Troubleshooting the cause of security and performance issues.
C. Reassembling fragmented traffic from raw data.
D. Detecting common hardware faults and identifying faulty assets.
E. Providing a historical record of a network transaction.
Correct Answer: CE
Question 3:
What is vulnerability management?
A. A security practice focused on clarifying and narrowing intrusion points.
B. A security practice of performing actions rather than acknowledging the threats.
C. A process to identify and remediate existing weaknesses.
D. A process to recover from service interruptions and restore business-critical applications
Correct Answer: C
Reference: https://www.brinqa.com/vulnerability-management-primer-part-2-challenges/
Vulnerability management is the “cyclical practice of identifying, classifying, prioritizing, remediating, and mitigating” software vulnerabilities.[1] Vulnerability management is integral to computer security and network security, and must not be confused with Vulnerability assessment” source: https://en.wikipedia.org/wiki/Vulnerability_management
Question 4:
Which type of attack is a blank email with the subject “price deduction” that contains a malicious attachment?
A. integrity violation
B. smishing
C. phishing attack
D. man-in-the-middle attack
Correct Answer: C
Question 5:
Which security principle is violated by running all processes as root or administrator?
A. principle of least privilege
B. role-based access control
C. separation of duties
D. trusted computing base
Correct Answer: A
Question 6:
How does agentless monitoring differ from agent-based monitoring?
A. Agentless can access the data via API. while agent-base uses a less efficient method and accesses log data through WMI.
B. Agent-based monitoring is less intrusive in gathering log data, while agentless requires open ports to fetch the logs
C. Agent-based monitoring has a lower initial cost for deployment, while agentless monitoring requires resource-intensive deployment.
D. Agent-based can locally filter and transmit only valuable data, while agentless has much higher network utilization
Correct Answer: D
Agent-based monitoring: With agent-based monitoring, software agents are installed on the monitored systems or devices. These agents collect data locally, perform filtering or preprocessing of the data, and then transmit the relevant or valuable information to the monitoring system. Agent-based monitoring allows for local processing and filtering, which can reduce network utilization by only transmitting essential data.
Agentless monitoring: Agentless monitoring, on the other hand, does not require software agents to be installed on the monitored systems or devices. Instead, it relies on leveraging existing protocols and interfaces, such as APIs (Application Programming Interfaces) or SNMP (Simple Network Management Protocol), to remotely access and retrieve monitoring data from the target systems. Agentless monitoring generally involves higher network utilization as the monitoring system needs to gather data from remote systems over the network.
Question 7:
What is the difference between deep packet inspection and stateful inspection?
A. Stateful inspection verifies contents at Layer 4. and deep packet inspection verifies connection at Layer 7.
B. Stateful inspection is more secure than deep packet inspection on Layer 7.
C. Deep packet inspection is more secure than stateful inspection on Layer 4.
D. Deep packet inspection allows visibility on Layer 7, and stateful inspection allows visibility on Layer 4.
Correct Answer: D
Question 8:
Which security technology allows only a set of pre-approved applications to run on a system?
A. application-level blacklisting
B. host-based IPS
C. application-level whitelisting
D. antivirus
Correct Answer: C
Question 9:
Which metric is used to capture the level of access needed to launch a successful attack?
A. privileges required
B. user interaction
C. attack complexity
D. attack vector
Correct Answer: D
Attack Vector ( AV) represents the level of access an attacker needs to have to exploit a vulnerability. It can assume four values: Network, Adjacent, Local, and Physical. Source: Official cert Guide Cisco CyberOps Associate CBROPS 200201 Chapter:
Introduction to Security Operations Management.
Question 10:
Refer to the exhibit.
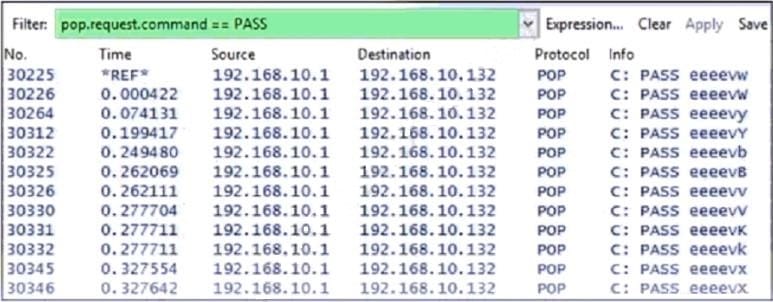
Which alert is identified from this packet capture?
A. man-in-the-middle attack
B. brute-force attack
C. ARP poisoning
D. SQL injection
Correct Answer: B
Question 11:
Which action should be taken if the system is overwhelmed with alerts when false positives and false negatives are compared?
A. Modify the settings of the intrusion detection system.
B. Design criteria for reviewing alerts.
C. Redefine signature rules.
D. Adjust the alert schedule.
Correct Answer: A
Traditional intrusion detection system (IDS) and intrusion prevention system (IPS) devices need to be tuned to avoid false positives and false negatives. Next-generation IPSs do not need the same level of tuning compared to traditional IPSs.
Also, you can obtain much deeper reports and functionality, including advanced malware protection and retrospective analysis to see what happened after an attack took place.
Ref: Cisco CyberOps Associate CBROPS 200-201 Official Cert Guide
Question 12:
What is indicated by an increase in IPv4 traffic carrying protocol 41?
A. additional PPTP traffic due to Windows clients
B. unauthorized peer-to-peer traffic
C. deployment of a GRE network on top of an existing Layer 3 network
D. attempts to tunnel IPv6 traffic through an IPv4 network
Correct Answer: D
Question 13:
Which technology prevents end-device-to-end-device IP traceability?
A. encryption
B. load balancing
C. NAT/PAT
D. tunneling
Correct Answer: C
Question 14:
What does the Zero Trust security model signify?
A. Zero Trust security means that no one is trusted by default from inside or outside the network.
B. Zero Trust addresses access control and states that an individual should have only the minimum access privileges necessary to perform specific tasks.
C. Zero Trust states that no users should be given enough privileges to misuse the system on their own.
D. Zero Trust states that unless a subject is given explicit access to an object, it should be denied access to that object.
Correct Answer: B
Question 15:
What is the difference between a threat and a risk?
A. Threat represents a potential danger that could take advantage of a weakness in a system
B. Risk represents the known and identified loss or danger in the system
C. Risk represents the nonintentional interaction with uncertainty in the system
D. Threat represents a state of being exposed to an attack or a compromise, either physically or logically.
Correct Answer: A
A threat is any potential danger to an asset. If a vulnerability exists but has not yet been exploited–or, more importantly, it is not yet publicly known–the threat is latent and not yet realized.
…
Summarize:
Leads4Pass shares some of the latest CyberOps Associate 200-201 Dumps exam questions online for free to help you test your current strength! Most importantly download the 2024 CyberOps Associate 200-201 Dumps: https://www.leads4pass.com/200-201.html, which contains 322 latest exam questions and answers, covering the complete 200-201 CBROPS certification exam content! It is the most important exam material to truly assist you in preparing for the 200-201 CBROPS certification exam.