The best and most Cisco CCNA Security 210-260 dumps exam training resources and study guides free download from leads4pass. 100% pass with new Cisco CCNA Security 210-260 dumps pdf materials and vce youtube demo free shared. “Implementing Cisco Network Security” is the name of Cisco CCNA Security https://www.leads4pass.com/210-260.html exam dumps which covers all the knowledge points of the real Cisco exam. Latest Cisco CCNA Security 210-260 dumps exam practice questions and answers update free try, pass Cisco 210-260 exam test easily.
New Cisco 210-260 dumps pdf materials free download: https://drive.google.com/open?id=0B_7qiYkH83VRcnI0SE83bHBvQ1k
New Cisco 210-451 dumps pdf materials free download: https://drive.google.com/open?id=0B_7qiYkH83VRQV9nZms0RGtyVGc
Vendor: Cisco
Certifications: CCNA Security
Exam Name: Implementing Cisco Network Security
Exam Code: 210-260
Total Questions: 310 Q&As
QUESTION 1
A specific URL has been identified as containing malware. What action can you take to block users from accidentally visiting the URL and becoming infected with malware.
A. Enable URL filtering on the perimeter router and add the URLs you want to block to the router’s local URL list.
B. Enable URL filtering on the perimeter firewall and add the URLs you want to allow to the router’s local URL list.
C. Enable URL filtering on the perimeter router and add the URLs you want to allow to the firewall’s local URL list.
D. Create a blacklist that contains the URL you want to block and activate the blacklist on the perimeter router.
E. Create a whitelist that contains the URLs you want to allow and activate the whitelist on the perimeter router.
Correct Answer: A
QUESTION 2
How can the administrator enable permanent client installation in a Cisco AnyConnect VPN firewall configuration?
A. Issue the command anyconnect keep-installer under the group policy or username webvpn mode
B. Issue the command anyconnect keep-installer installed in the global configuration
C. Issue the command anyconnect keep-installer installed under the group policy or username webvpn mode
D. Issue the command anyconnect keep-installer installer under the group policy or username webvpn mode
Correct Answer: C
QUESTION 3
When a company puts a security policy in place, what is the effect on the company’s business?
A. Minimizing risk
B. Minimizing total cost of ownership
C. Minimizing liability
D. Maximizing compliance
Correct Answer: A
QUESTION 4
In which stage of an attack does the attacker discover devices on a target network? 210-260 dumps
A. Reconnaissance
B. Covering tracks
C. Gaining access
D. Maintaining access
Correct Answer: A
QUESTION 5
Refer to the exhibit.
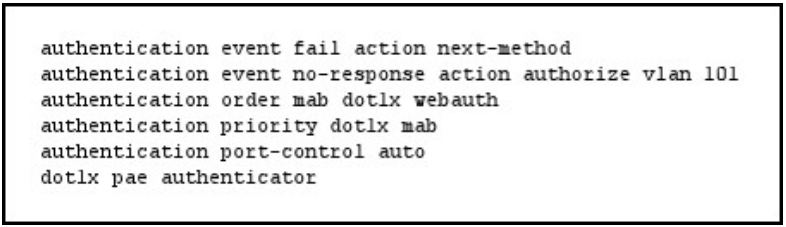
If a supplicant supplies incorrect credentials for all authentication methods configured on the switch, how will the switch respond?
A. The supplicant will fail to advance beyond the webauth method.
B. The switch will cycle through the configured authentication methods indefinitely.
C. The authentication attempt will time out and the switch will place the port into the unauthorized state.
D. The authentication attempt will time out and the switch will place the port into VLAN 101.
Correct Answer: A
QUESTION 6
Which Cisco product can help mitigate web-based attacks within a network?
A. Adaptive Security Appliance
B. Web Security Appliance
C. Email Security Appliance
D. Identity Services Engine
Correct Answer: B
QUESTION 7
Which tasks is the session management path responsible for? (Choose three.)
A. Verifying IP checksums
B. Performing route lookup
C. Performing session lookup
D. Allocating NAT translations
E. Checking TCP sequence numbers
F. Checking packets against the access list
Correct Answer: BDF
QUESTION 8
Refer to the exhibit.
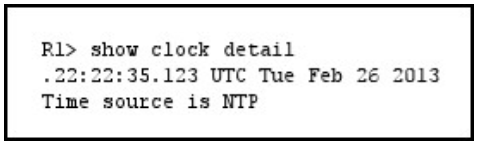
Which statement about the device time is true?
A. The time is authoritative, but the NTP process has lost contact with its servers.
B. The time is authoritative because the clock is in sync.
C. The clock is out of sync.
D. NTP is configured incorrectly.
E. The time is not authoritative.
Correct Answer: A
QUESTION 9
210-260 dumps Which EAP method uses Protected Access Credentials?
A. EAP-FAST
B. EAP-TLS
C. EAP-PEAP
D. EAP-GTC
Correct Answer: A
QUESTION 10
Which feature of the Cisco Email Security Appliance can mitigate the impact of snowshoe spam and sophisticated phishing attacks?
A. contextual analysis
B. holistic understanding of threats
C. graymail management and filtering
D. signature-based IPS
Correct Answer: A
QUESTION 11
What is one requirement for locking a wired or wireless device from ISE?
A. The ISE agent must be installed on the device.
B. The device must be connected to the network when the lock command is executed.
C. The user must approve the locking action.
D. The organization must implement an acceptable use policy allowing device locking.
Correct Answer: A
QUESTION 12
Which statement about extended access lists is true?
A. Extended access lists perform filtering that is based on source and destination and are most effective when applied to the destination
B. Extended access lists perform filtering that is based on source and destination and are most effective when applied to the source
C. Extended access lists perform filtering that is based on destination and are most effective when applied to the source
D. Extended access lists perform filtering that is based on source and are most effective when applied to the destination
Correct Answer: B
Read more: https://www.leads4pass.com/210-260.html dumps exam questions and answers update free shared, the best and most Cisco CCNA Security 210-260 dumps pdf training materials free update.
Latest leads4pass 210-260 dumps vce youtube demo: https://youtu.be/seDmEyXcd3w