The latest updated October 2022 350-401 dumps PDF and VCE from leads4pass for the CCNP Enterprise Core exam. Welcome to download the latest leads4pass 350-401 VCE and PDF dumps:https://www.leads4pass.com/350-401.html (866 Q&As)
Free 350-401 dumps PDFs are available on the Google Drive shared by leads4pass:
[Updated Free.1] https://drive.google.com/file/d/1fYt1qLwW_w51z4Gr4pUOqVnyab6Ioeg3/
[Updated Free.2] https://drive.google.com/file/d/1UZ1OCWXuClKs73-SDQXFO8j-oA4A8a8Q/
[Updated Free.3] https://drive.google.com/file/d/1CzUD7IShCoh1JNUYek2Q2REVIzJprjMs/
[Updated Free.4] https://drive.google.com/file/d/1ahrnRyvF4ubbTamp6ejufmuvDDV3xA_H/
leads4pass 350-401 exam questions are shared on a timeline to stay up to date!
| Exam name | Number of exam questions | From | Release time |
| Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) | 15 | leads4pass | Oct 07, 2022 |
How does Cisco Trustsec enable more access controls for dynamic networking environments and data centers?
A. uses flexible NetFlow
B. assigns a VLAN to the endpoint
C. classifies traffic based on the contextual identity of the endpoint rather than its IP address
D. classifies traffic based on advanced application recognition
Correct Answer: C
The Cisco TrustSec solution simplifies the provisioning and management of network access control through the use of software-defined segmentation to classify network traffic and enforce policies for more flexible access controls. Traffic classification is based on endpoint identity, not IP address, enabling policy change without network redesign.
Which technology provides a secure communication channel for all traffic at Layer 2 of the OSI model?
A. MACsec
B. IPsec
C. SSL
D. Cisco Trustsec
Correct Answer: A
MACsec, defined in 802.1AE, provides MAC-layer encryption over wired networks by using out- of band methods for encryption keying.
The MACsec Key Agreement (MKA) Protocol provides the required session keys and manages the required encryption keys.
MKA and MACsec are implemented after successful authentication using the 802.1x Extensible Authentication Protocol (EAP-TLS) or Pre Shared Key (PSK) framework.
A switch using MACsec accepts either MACsec or non-MACsec frames, depending on the policy associated with the MKA peer. MACsec frames are encrypted and protected with an integrity check value (ICV).
When the switch receives frames from the MKA peer, it decrypts them and calculates the correct ICV by using session keys provided by MKA.
The switch compares that ICV to the ICV within the frame. If they are not identical, the frame is dropped.
The switch also encrypts and adds an ICV to any frames sent over the secured port (the access point used to provide the secure MAC service to an MKA peer) using the current session key.
Note: Cisco Trustsec is the solution that includes MACsec.
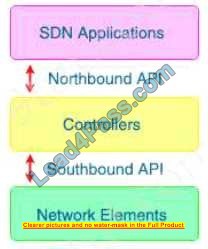
What does Cisco DNA southbound APIs provide?
A. Interface between the controller and the network devices
B. NETCONF API interface for orchestration communication
C. RESful API interface for orchestrator communication
D. Interface between the controller and the consumer
Correct Answer: A
The Southbound API is used to communicate with network devices.
Which NGFW mode block flows crossing the firewall?
A. Passive
B. Tap
C. Inline tap
D. Inline
Correct Answer: D
Firepower Threat Defense (FTD) provides six interface modes which are: Routed, Switched, Inline Pair, Inline Pair with Tap, Passive, and Passive (ERSPAN). When Inline Pair Mode is in use, packets can be blocked since they are processed inline When you use Inline Pair mode, the packet goes mainly through the FTD Snort engine When Tap Mode is enabled, a copy of the packet is inspected and dropped internally while the actual traffic goes through FTD unmodified
Which two pieces of information are necessary to compute SNR? (Choose two.)
A. EIRP
B. noise floor
C. antenna gain
D. RSSI
E. transmit power
Correct Answer: BD
signal-to-noise ratio (SNR) A measure of received signal quality, calculated as the difference between the signal\’s RSSI and the noise floor. A higher SNR is preferred.
Which requirement for an Ansible-managed node is true?
A. It must be a Linux server or a Cisco device.
B. It must have an SSH server running.
C. It must support ad hoc commands.
D. It must have an Ansible Tower installed.
Correct Answer: B
What is the difference between the enable password and the enable secret password when password encryption is enabled on an IOS device?
A. The enable password is encrypted with a stronger encryption method.
B. There is no difference and both passwords are encrypted identically.
C. The enable password cannot be decrypted.
D. The enable secret password is protected via stronger cryptography mechanisms.
Correct Answer: D
The “enable secret” password is always encrypted (independent of the “service passwordencryption” command) using MD5 hash algorithm.
The “enable password” does not encrypt the password and can be view in clear text in the running-config. In order to encrypt the “enable password”, use the “service password-encryption” command. This command will encrypt the passwords by using the Vigenere encryption algorithm.
Unfortunately, the Vigenere encryption method is cryptographically weak and trivial to reverse.
The MD5 hash is a stronger algorithm than Vigenere so answer \’ The enable secret password is protected via stronger cryptography mechanisms\’ is correct.
Which configuration establishes EBGP neighborship between these two directly connected neighbors and exchanges the loopback network of the two routers through BGP?

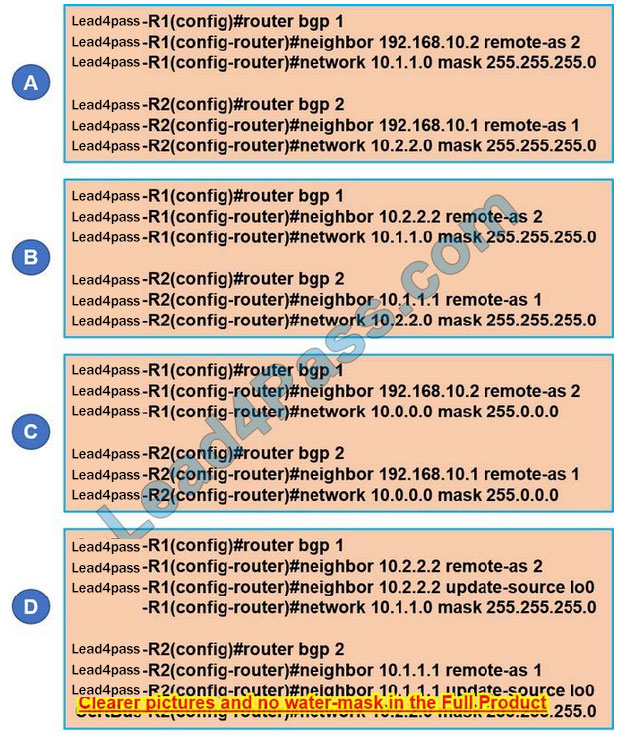
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: A
With BGP, we must advertise the correct network and subnet mask in the “network” command (in this case network 10.1.1.0/24 on R1 and network 10.2.2.0/24 on R2). BGP is very strict in routing advertisements. In other words, BGP only advertises the network which exists exactly in the routing table. In this case, if you put the command “network x.x.0.0 mask 255.255.0.0” or “network x.0.0.0 mask 255.0.0.0” or “network x.x.x.x mask 255.255.255.255” then BGP will not advertise anything. It is easy to establish eBGP neighborship via the direct link. But let\’s see what is required when we want to establish eBGP neighborship via their loopback interfaces. We will need two commands:
+
the command “neighbor 10.1.1.1 ebgp-multihop 2” on R1 and “neighbor 10.2.2.2 ebgpmultihop 2” on R1. This command increases the TTL value to 2 so that BGP updates can reach the BGP neighbor which is two hops away.
+
Answer `R1 (config) #router BGP 1 R1 (config-router) #neighbor 192.168.10.2 remote-as 2 R1 (config-router) #network 10.1.1.0 mask 255.255.255.0 R2 (config) #router BGP 2 R2 (config-router) #neighbor 192.168.10.1 remote-as 1 R2 (config-router) #network 10.2.2.0 mask 255.255.255.0 Quick Wireless Summary Cisco Access Points (APs) can operate in one of two modes: autonomous or lightweight + Autonomous: self-sufficient and standalone. Used for small wireless networks. + Lightweight: A Cisco lightweight AP (LAP) has to join a Wireless LAN Controller (WLC) to function. Do LAP and WLC communicate with each other via a logical pair of CAPWAP tunnels. ?Control and Provisioning for Wireless Access Point (CAPWAP) is an IETF standard for control messaging for setup, authentication, and operations between APs and WLCs. CAPWAP is similar to LWAPP except for the following differences: +CAPWAP uses Datagram Transport Layer Security (DTLS) for authentication and encryption to protect traffic between APs and controllers. LWAPP uses AES. + CAPWAP has a dynamic maximum transmission unit (MTU) discovery mechanism. + CAPWAP runs on UDP ports 5246 (control messages) and 5247 (data messages) An LAP operates in one of six different modes:
+
Local mode (default mode): measures noise floor and interference, and scans for intrusion detection (IDS) events every 180 seconds on unused channels + FlexConnect, formerly known as Hybrid Remote Edge AP (H-REAP), mode: allows data traffic to be switched locally and not go back to the controller. The FlexConnect AP can perform standalone client authentication and switch VLAN traffic locally even when it\’s disconnected from the WLC (Local Switched). FlexConnect AP can also tunnel (via CAPWAP) both user wireless data and control traffic to a centralized WLC (Central Switched).
+
Monitor mode: does not handle data traffic between clients and the infrastructure. It acts like a sensor for location-based services (LBS), rogue AP detection, and IDS + Rogue detector mode: monitor for rogue APs. It does not handle data at all. + Sniffer mode: run as a sniffer and captures and forwards all the packets on a particular channel to a remote machine where you can use protocol analysis tools (Wireshark, Airopeek, etc) to review the packets and diagnose issues. Strictly used for troubleshooting purposes. + Bridge mode: bridge together the WLAN and the wired infrastructure together. Mobility Express is the ability to use an access point (AP) as a controller instead of a real WLAN controller. But this solution is only suitable for small to midsize, or multi-site branch locations where you might not want to invest in a dedicated WLC. A Mobility Express WLC can support up to 100 Apps
In which part of the HTTP message is the content type specified?
A. HTTP method
B. URI
C. header
D. body
Correct Answer: C
Reference: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Type
Which behavior can be expected when the HSRP versions are changed from 1 to 2?
A. Each HSRP group reinitializes because the virtual MAC address has changed.
B. No changes occur because versions 1 and 2 use the same virtual MAC OUI.
C. Each HSRP group reinitializes because the multicast address has changed.
D. No changes occur because the standby router is upgraded before the active router.
Correct Answer: A
A response code of 404 is received while using the REST API on Cisco UNA Center to POST to this URI.
/DNA/intent/API/v1 /template-programmer/project
What does the code mean?
A. The client made a request for a resource that does not exist.
B. The server has not implemented the functionality that is needed to fulfill the request.
C. The request was accepted for processing, but the processing was not completed.
D. The POST/PUT request was fulfilled and a new resource was created, Information about the resource is in the response body.
Correct Answer: A
The 404 (Not Found) error status code indicates that the REST API can\’t map the client\’s URI to a resource but may be available in the future. Subsequent requests by the client are permissible.
Reference: https://restfulapi.net/http-status-codes/
What is the structure of a JSON web token?
A. three parts separated by dots header payload, and signature
B. header and payload
C. three parts separated by dots version header and signature
D. payload and signature
Correct Answer: A
JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way
for securely transmitting information between parties as a JSON object. This information can be verified
and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or
a public/private key pair using RSA or ECDSA. JSON Web Tokens are composed of three parts, separated
by a dot (.): Header, Payload, and Signature. Therefore, a JWT typically looks like the following:
xxxxx.yyyyy.zzzzz
The header typically consists of two parts: the type of the token, which is JWT, and the signing algorithm
being used, such as HMAC SHA256 or RSA.
The second part of the token is the payload, which contains the claims. Claims are statements about an
entity (typically, the user) and additional data. To create the signature part you have to take the encoded
header, the encoded payload, a secret, and the algorithm specified in the header, and sign that.
Reference:
https://auth0.com/docs/tokens/references/jwt-structure
Which OSPF network types are compatible and allow communication through the two peering devices?
A. broadcast to nonbroadcast
B. point-to-multipoint to nonbroadcast
C. broadcast to point-to-point
D. point-to-multipoint to broadcast
Correct Answer: A
The following different OSPF types are compatible with each other:
+ Broadcast and Non-Broadcast (adjust hello/dead timers) + Point-to-Point and Point-to-Multipoint (adjust hello/dead timers) Broadcast and Non-Broadcast networks elect DR/BDR so they are compatible.
Pointtopoint/ multipoint do not elect DR/BDR so they are compatible.
Reference: https://www.freeccnaworkbook.com/workbooks/ccna/configuring-ospf-network-types
At which Layer does Cisco DNA Center support REST controls?
A. EEM applets or scripts
B. Session layer
C. YMAL output from responses to API calls
D. Northbound APIs
Correct Answer: D
Which statement about agent-based versus agentless configuration management tools is true?
A. Agentless tools require no messaging systems between master and slaves.
B. Agentless tools use proxy nodes to interface with slave nodes.
C. Agent-based tools do not require a high-level language interpreter such as Python or Ruby on slave nodes.
D. Agent-based tools do not require the installation of additional software packages on the slave nodes.
Correct Answer: A
…
The latest updated October 2022 350-401 dumps PDF and VCE from leads4pass for the CCNP Enterprise Core exam. Welcome to download the latest leads4pass 350-401 VCE and PDF dumps:https://www.leads4pass.com/350-401.html (866 Q&As)
Free 350-401 dumps PDFs are available on the Google Drive shared by leads4pass:
[Updated Free.1] https://drive.google.com/file/d/1fYt1qLwW_w51z4Gr4pUOqVnyab6Ioeg3/
[Updated Free.2] https://drive.google.com/file/d/1UZ1OCWXuClKs73-SDQXFO8j-oA4A8a8Q/
[Updated Free.3] https://drive.google.com/file/d/1CzUD7IShCoh1JNUYek2Q2REVIzJprjMs/
[Updated Free.4] https://drive.google.com/file/d/1ahrnRyvF4ubbTamp6ejufmuvDDV3xA_H/